Tailscale has raised a $12 million funding round. Accel is leading the round with Heavybit and Uncork Capital also participating. The company is building a better corporate VPN by leveraging a modern protocol and focusing on ease of implementation.
A VPN, or a virtual private network, is an encrypted tunnel between two devices. Many companies rely on a VPN for remote employees, multi-office setups and internal services that are supposed to be visible to employees exclusively. For instance, if you’re working remotely, chances are you can connect to your company’s intranet and internal services by connecting to a VPN server from your corporate laptop.
Over the past few years, there have been multiple trends when it comes to accessing your company’s internal network. Some companies rely on sophisticated access policies. Google has been going down this path with its BeyondCorp zero trust system.
Other companies still rely on corporate VPNs and firewalls as they are easy to implement. They often use the IPsec protocol with a VPN gateway that handles the connection to the internal network.
If you’ve been working remotely lately, you may have noticed that this traditional VPN setup doesn’t scale well. The gateway is a bottleneck and you can experience long loading times when there are a lot of people connected at the same time.
Going back to Tailscale, the startup is trying to modernize the corporate VPN. It starts with a different VPN protocol. Tailscale chose WireGuard, a lightweight VPN protocol that relies on a combination of public and private keys to establish an encrypted tunnel between two clients.
But Wireguard itself is just a protocol. It doesn’t tell you how you’re supposed to handle public keys, add new devices to your network, etc. Tailscale acts as the glue that brings all the separate pieces together.
"Architecturally, I would describe Tailscale as the Control Plane and WireGuard is the data plane,” co-founder and CEO Avery Pennarun told me.
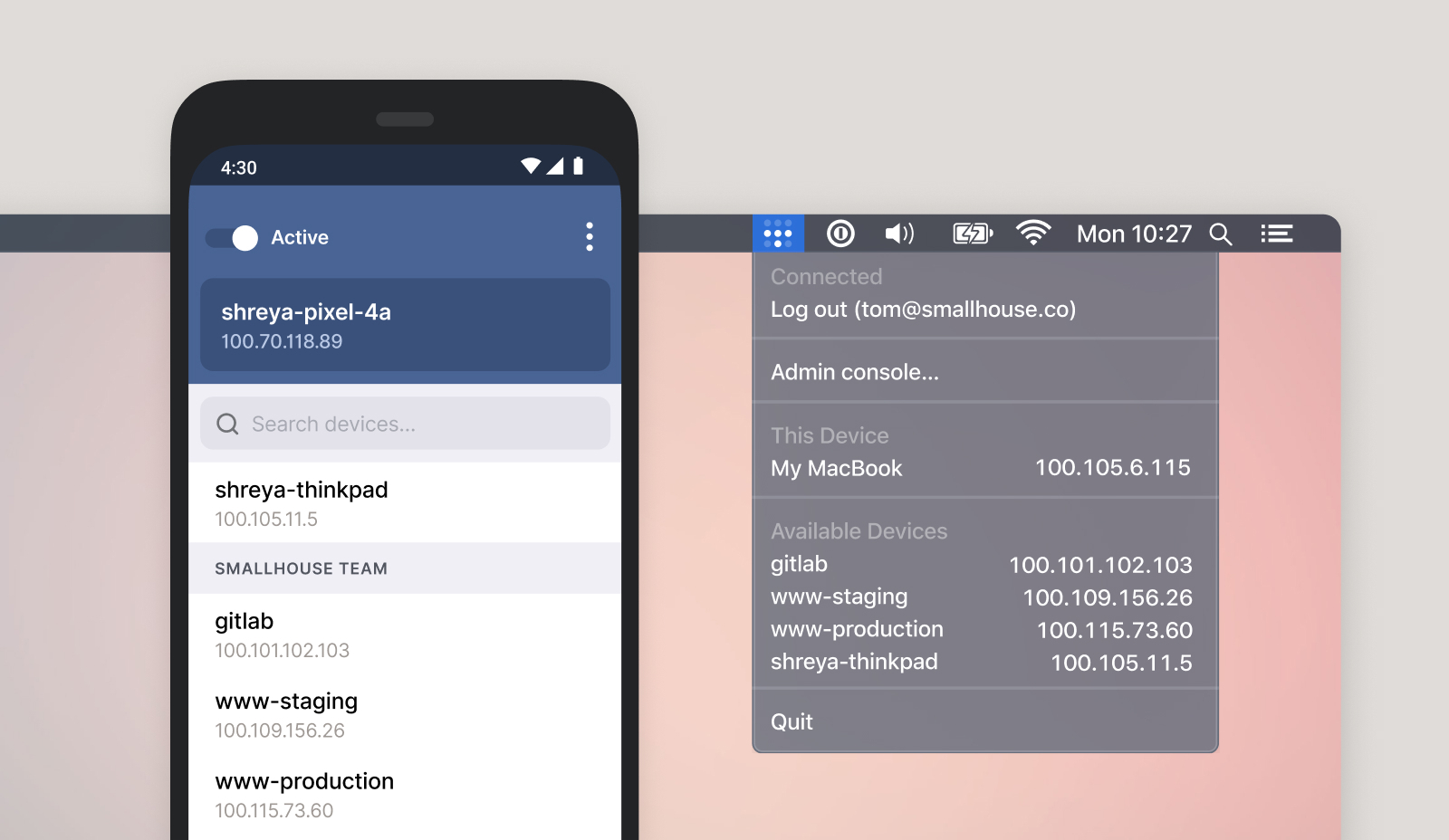
Image Credits: Tailscale
Let’s take an example. Your company has an internal Git server and an internal documentation wiki. You have a corporate laptop and you want to access those two services. You can install the Tailscale client on three different machines — your laptop, the Git server and the wiki server.
When you want to connect to the internal services, Tailscale asks you to log in using your company’s identity provider, such as G Suite, Okta, Active Directory, etc.
All Tailscale clients check a coordination server to see if the connection is authorized. “It’s a drop box for public keys,” Pennarun said. When somebody leaves the company, the public key is removed from the coordination server and Tailscale no longer works. Keys are rotated regularly for improved security.
A connection is then established between your laptop and the Git server or your laptop and the wiki server. There’s no bottleneck due to the VPN gateway as the Git server and the wiki server act as their own VPN gateways. There’s no need to expose your documentation wiki to the internet as employees first use Tailscale to access the server.
You don’t have to open the SSH port on the server as Tailscale can find a way to establish a connection through firewalls.
The company is still quite small but pretty efficient. With around 20 employees, Tailscale is generating tens of thousands of client installs per month.
You can get started for free with a single user and multiple devices. Some users have tried it with a Raspberry Pi at home so that they can connect to their local network when they’re on the move. They bring it to work later.
By keeping customer acquisition costs very low, Tailscale has managed to raise $12 million. Twingate is another company trying to solve the same issue, but it has made different technical choices — they rely on TLS tunnels and relays.
from TechCrunch https://ift.tt/2UdAhXC
via IFTTT

Post a Comment